Known issues in Cloudera Data Warehouse on premises 1.5.4 SP2
Review the issues identified in this service pack release of Cloudera Data Warehouse on premises.
- DWX-20085: Non-admin user in Cloudera Data Visualization loses all roles and permissions
- When a non-admin user who does not belong to any group in Cloudera Management Console logs in to Cloudera Data Visualization for the first
time, the user is assigned to the "viz_guest_group" default group in Cloudera Data Visualization and is assigned the "Database Admin" role.
Subsequent logins remove all the groups associated with the user in Cloudera Data Visualization and only the groups that come from SAML assertion are assigned to the user. This can in turn lead to the user losing all privileges on the Cloudera Data Visualization instance.
- DWX-20849: Multiple stateful set pods failing failing after node restart
- After a node restart, some Cloudera Data Warehouse
stateful set pods may become stuck in the initializing phase and display the following
error:
Unable to retrieve some image pull secrets (docker-image-pull-secret); attempting to pull the image may not succeed.The stateful set pods affected by this issue include -
huebackend,hiveserver2,metastore, andcoordinator. - DWX-20925: Unable to forward Impala audit logs to HDFS
- A
kinitcommand in the Impala Coordinator pod, specifically under theaudit-logs-fluentdcontainer, fails with the following error -Cryptosystem internal error while getting initial credentials.As a result, Impala audit logs are not forwarded to HDFS. The issue is caused due to a problem with a chainguard base image.
- DWX-21088: Impala Virtual Warehouse with Unified Analytics mode triggers 'KubeStatefulSetReplicasMismatch' errors
- When creating an Impala Virtual Warehouse within Cloudera Data Warehouse without setting the Active-Active HA mode, error messages are displayed by the Monitoring application, either on the OpenShift Alarm page or in the Cloudera Management Console Dashboard with the 'KubeStatefulSetReplicasMismatch' message.
- Case sensitivity issue for Ranger authentication
- In Active Directory environments, user and group names are often
written in mixed case (for example, 'JohnDoe' or 'AdminGroup') and handled in a
case-insensitive manner by Windows. However, Cloudera Base on premises operates in a Linux environment, where names
are case-sensitive. To address this, some customers configure Cloudera Base on premises to disable case sensitivity in System
Security Service Daemon (sssd) and modify Ranger Usersync settings to convert user and group
names to lowercase, ensuring compatibility with Ranger policies.
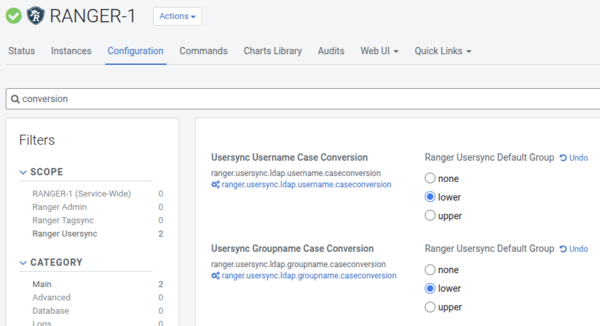
While this configuration works correctly in Cloudera Base on premises, authorization issues may arise inCloudera Data Warehouse components like Hive and Impala. Cloudera Data Warehouse does not automatically convert group names to lowercase, causing mismatches with Ranger policies that define group names in lowercase. This can result in authorization problems, such as users being unable to access databases, tables, or columns in Hue or remote client shells (impala-shell or jdbc), even though access works correctly in Cloudera Base on premises Hue or remote client shells.
